Understanding DDoS Attacks: A Comprehensive Guide
Understanding DDoS Attacks: A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic. DDoS attacks have become increasingly common in recent years and can be very disruptive and damaging to organizations. This comprehensive guide provides an in-depth look at DDoS attacks, how they work, their history and evolution, major events and statistics, common targets, motivations behind attacks, and prevention and mitigation strategies.
What is a DDoS Attack?
A Distributed Denial of Service attack is executed by multiple compromised systems which are often infected with malware. The flood of incoming messages to the target system essentially forces it to shut down, thereby denying service to legitimate users or systems.
These compromised computer systems used to carry out DDoS attacks are often referred to as 'botnets' or 'zombie armies'. Botnets comprise internet-connected devices that have been infected with malicious software and controlled remotely by an attacker. When given a command, these compromised devices will together attempt to overwhelm a target with fake traffic to take it offline.
Some key characteristics of DDoS attacks:
- The goal is to disrupt the services of a host connected to the internet
- Achieved by flooding the target with an unsustainable amount of traffic
- Traffic originates from many different sources (distributed)
- Renders target inaccessible to its intended users
- Can last from several minutes to even weeks
- Botnets used to orchestrate attack traffic
How Do DDoS Attacks Work?
A DDoS attack is similar to a traffic jam clogging up highways, preventing regular traffic from arriving at its destination. It essentially overwhelms the target infrastructure with an enormous volume of fake traffic, so that legitimate requests cannot get through. This eventually causes denial of service for users of the targeted resource.
There are several ways a DDoS attack can be carried out to bring down a system:
Volume-based Attacks
This involves flooding the bandwidth of the target network or service with huge amounts of bogus traffic. The inbound traffic congestion overwhelms the target's bandwidth and resources, making it unreachable to legitimate users.
Protocol Attacks
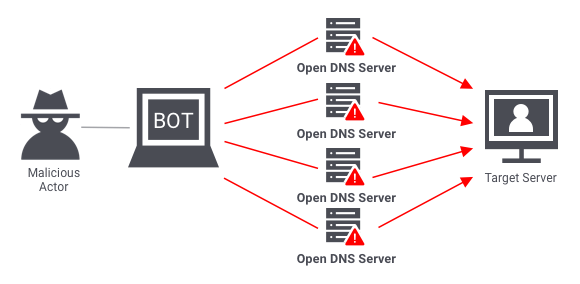
These attacks focus on exhausting resources of network components like load balancers, web servers, and application servers by exploiting vulnerabilities in protocol implementations. For example, a DNS amplification attack uses misconfigured DNS servers to overwhelm a target with DNS response traffic.
Application Layer Attacks
Such attacks target web servers and application resources by sending non-existent pages, slowing down database read/write capabilities, etc which crashes web servers and applications. For instance, an HTTP flood attack overwhelms web servers with valid yet high volumes of HTTP requests.
Reflection and Amplification Attacks
These attacks use publicly accessible services to reflect and amplify a relatively small attack into a much larger one. The traffic is bounced off intermediary servers to the target using the spoofed IP address of the victim. This hides the source of the attack while enabling leveraging of traffic amplification.
So in summary, DDoS attacks subdue systems with the brute force of massive traffic coming from different sources. This eventually overloads resources and prevents legitimate requests from being fulfilled.
A Brief History of DDoS Attacks
Distributed denial of service attacks began emerging in the late 1990s once botnets became popular. Some major historical events and developments include:
- One of the very first instances of a DDoS attack took place in 1999 against the University of Minnesota which received huge amounts of unwanted requests that overloaded its internet connection.
- In 2000, major DDoS attacks brought down big names like eBay, Amazon, CNN and other major websites. These attacks were carried out by a Canadian high school student using botnets.
- In 2001, researcher Paul Barford observed that virus-infected Windows machines were being increasingly used to launch DDoS attacks utilizing spoofed IP addresses.
- The early to mid-2000s saw the rise of large-scale botnets like Agobot, MyDoom, and SDBot which were used to execute lucrative DDoS attacks and extortion schemes.
- In 2007, Estonian organizations faced prolonged DDoS attacks allegedly carried out by Russian hackers upset about the removal of a Soviet-era war memorial. This was one of the first instances of massive disruption of an entire nation's internet.
- By 2010, short but powerful DDoS bursts were being used to bring down banking and financial institution websites. The perpetrators included activist groups like Anonymous and Lizard Squad.
- DDoS techniques evolved by 2012-13 with complex application layer attacks directed against web application vulnerabilities rather than just flooding networks. High-profile victims included US banks.
- The Mirai botnet emerged in 2016 and was responsible for some of the largest DDoS attacks ever recorded, exceeding 1 Tbps traffic and bringing down major internet platforms.
- DDoS events targeting elections and political campaigns started seeing rises in 2016. Alleged nation-state actors utilized DDoS as a cyber warfare technique.
- Cryptocurrency platforms became prime targets in 2017. DDoS extortionists demanded ransoms in digital currencies from exchanges, often attempting to manipulate crypto prices.
- By 2021, ransom DDoS or RDoS had emerged as the top motivation behind increasing DDoS attacks. Extortion demands averaging over $200,000 were made against organizations globally.
So in summary, DDoS attacks rapidly evolved from basic flooding incidents to nation-state-sponsored cyber warfare and organized criminal extortion campaigns over the past two decades. Their disruptive impact dramatically increased in scale, sophistication, and frequency during this period.
DDoS Attack Statistics and Trends
Some key statistics and trends highlight the current DDoS threat landscape:
- Multi-vector DDoS attacks combining multiple attack vectors have grown enormously. 98% of organizations faced such multi-vector attacks according to Neustar.
- Attack traffic bandwidths reached record levels in 2021. The largest reported DDoS attack was 17.2 million requests per second (MRPS).
- Extortion is the top motivation today behind 78% of DDoS attacks as per monitoring firm Netscout. Ransom demands average around $250,000.
- DDoS botnets are increasingly made up of non-traditional devices. 16% comprise IoT devices as per Kaspersky. Camera and router botnets are common.
- Attack durations averaged 5 days according to Kaspersky. But they may last for weeks, designed to cause maximum disruption until a ransom is paid.
- Gaming firms faced the most DDoS attacks in 2021 as per Kaspersky, followed by software companies and then banks and payment services.
- Threat actors include hacktivists, cybercriminals, nation-states, and even business competitors. Attacks may also originate from resentful customers or former employees.
- DDoS threats are increasing across mobile networks as well. Such attacks against 5G networks grew 54% YoY in 2021 as per Ericsson.
- Damages include revenue losses averaging $250K per DDoS attack as per a Neustar survey. Reputational damage and customer churn are other major consequences.
So in summary, today's DDoS threat landscape is extremely risky for organizations. Multi-vector attacks of higher sophistication and scale are being launched for extortion and disruption. A wide range of threat actors are motivated to carry out such attacks using new attack surfaces like mobile networks and IoT botnets. This makes DDoS one of the top cybersecurity risks faced by modern enterprises.
Common Targets of DDoS Attacks
Though any organization connected online is vulnerable, some typical prime targets for DDoS include:
- Banks and Financial Institutions - Bringing down banking web portals and mobile apps provides motivation both for cybercriminals looking for extortion income as well as hacktivists wanting to disrupt finances.
- Government Agencies - Online services of government bodies have often been disrupted by DDoS, especially by hacktivists and state actors. Attacks against elections and voter registration systems have also been observed.
- Media and Entertainment - Broadcasters, publishers, and platforms have faced DDoS attacks from various threat actors wanting to take down websites and disrupt streaming services.
- Cloud Service Providers - Large DDoS attacks against public cloud networks and services are a major risk today. AWS, Azure, and Google Cloud have all faced record attacks.
- Gaming Industry - Online gaming networks are highly lucrative DDoS targets, since even small disruptions hemorrhage customers and revenue.
- E-commerce - Online retailers have faced high volumes of DDoS over the years, often near busy shopping days, extorting ransoms to avoid sales losses.
- Telecom Providers - Attacks have brought down the internet, mobile, and VoIP services. 5G networks are an emerging target. Disrupting connectivity has major cascading effects.
- Transportation - Railways, airlines, and logistic companies relying on online services have been impacted by DDoS, especially state-sponsored attacks.
So organizations across sectors offering critical online services are prime targets today for DDoS attackers wanting to cause maximum disruption and extortion impact.
Motivations Behind DDoS Attacks
Various motivations drive different actors to carry out DDoS attacks:
- Financial Gain - Cybercriminals execute attacks to extort ransom payments from target organizations. Even short disruptions of revenue-critical services can make victims pay up.
- Revenge - Disgruntled customers, ex-employees, or online gamers may launch DDoS to punish organizations that they have some revenge motive against.
- Hacktivism - Activist groups like Anonymous often launch DDoS attacks for political and social causes against government and commercial entities.
- Competitive Advantage - Unscrupulous business rivals may seek competitive intelligence or disruption of performance by taking down competitor websites and services.
- Cyberwarfare - State-sponsored attackers utilize DDoS campaigns for geopolitical, military, and strategic objectives during conflicts by targeting critical national infrastructure.
- Damage/Destruction - Vandalism of networks and services via DDoS is also done simply to cause damage without any particular motives.
So organizations today face a variety of external and internal adversaries seeking financial, activist, military, or other goals via DDoS attacks. Understanding these motives is key to recognizing the most likely threats they are vulnerable to.
DDoS Prevention and Mitigation Strategies
Organizations can deploy several countermeasures to prevent and mitigate DDoS impact:
- Network Traffic Monitoring - Real-time monitoring helps quickly detect anomalies and patterns indicating potential DDoS activity. Rate limiting identifies suspicious spikes.
- IP Reputation Filtering - Databases of known malicious IP addresses engaging in past DDoS behavior allow blocking traffic originating from them.
- Overprovision Bandwidth - Having excess bandwidth makes networks more resilient against flooding attacks aiming to saturate capacity. It enables absorbing sudden traffic spikes.
- Load Balancing - Distributing traffic across multiple servers avoids overloading specific targets. It provides additional capacity to deal with DDoS floods.
- Web Application Firewalls - WAFs offer application layer protection against malformed queries, slow POST attacks, and other application attacks.
- Blackhole Routing - Diverting attack traffic towards blackhole routes keeps critical infrastructure available to legitimate users during an attack.
- DDoS Mitigation Services - Specialized third-party services absorb and cleanse attack traffic on their scrubbing centers before passing legitimate traffic to customers.
- Multi-Layered Security - Combining network, application, hardware, and other security layers provides overlapping defenses for maximum protection.
- Emergency Response Planning - Incident response plans that outline procedures, teams, and communication channels allow rapid coordinated reaction to DDoS events.
- Employee/Customer Training - Educating employees and customers on DDoS threats helps them play their role in prevention and mitigation.
A capable and tested DDoS defense requires a combination of proactive and reactive techniques across networks, applications, hardware, and processes for effective risk reduction.
Conclusion
DDoS represents one of the most serious cyber threats faced by modern digital businesses with catastrophic impacts possible on revenue and reputation. As attacks grow more frequent, sophisticated, and damaging, organizations must make DDoS resilience a top priority. A multi-layered defense has to be deployed through a combination of capable in-house security teams, robust network and application architectures, and specialist-managed security services. DDoS can no longer be ignored or underestimated on the cyber risk register. Proactively developing capabilities to deter, prevent, detect, and mitigate DDoS attacks is essential to survive in today's threat landscape.

Comments
Post a Comment